X Forwarded Firefox
- X Forwarded Firefox Extension
- X Forwarded Firefox Settings
- X Forwarded Firefox Download
- X Forwarded Firefox To Yahoo
- X Forwarded Firefox Browser
- X Forwarded Firefox To Google
Topics
X Forwarded Firefox Extension
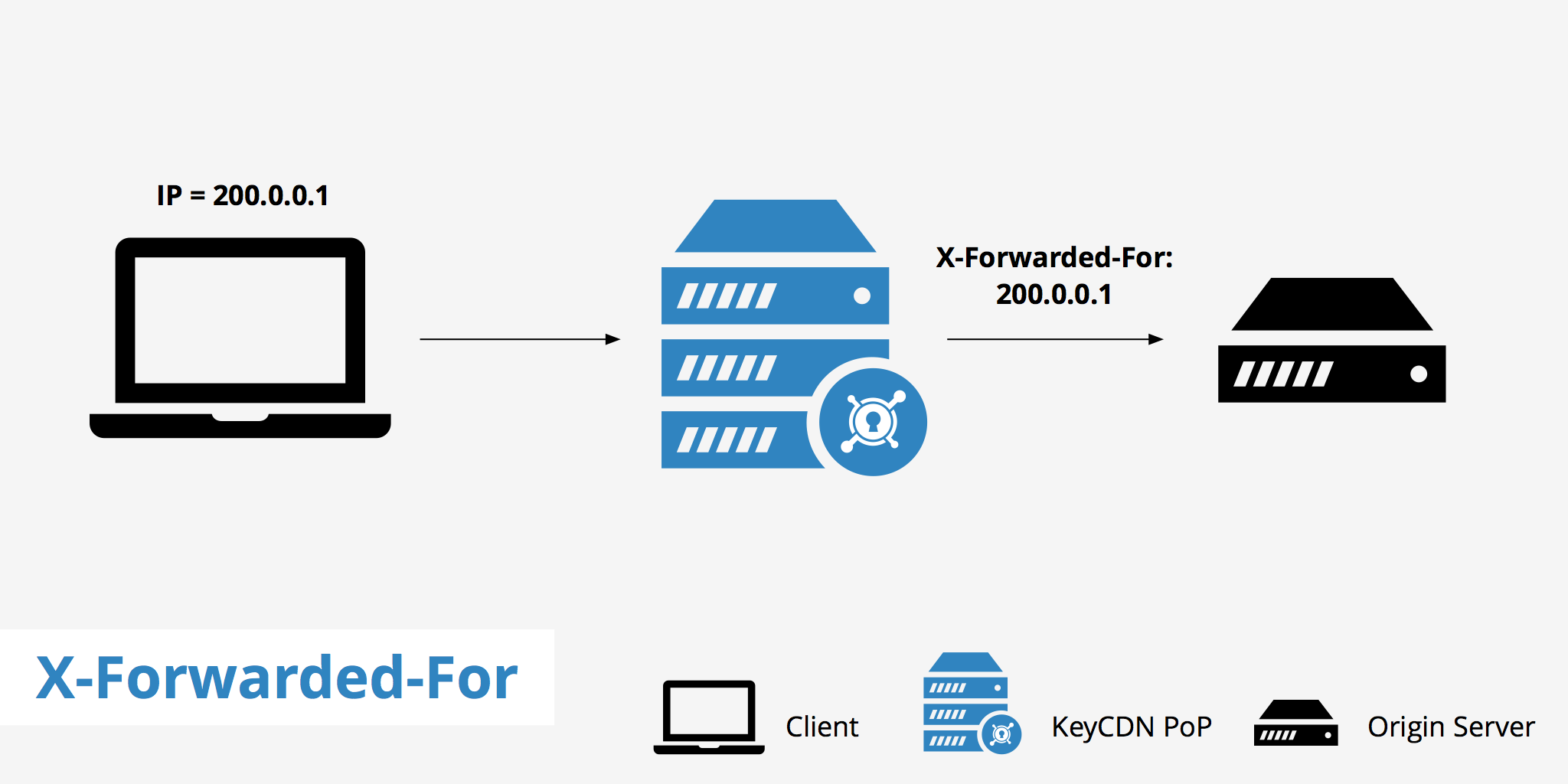
Local File Security in Firefox 68 When a user opened a page using a file:/// URI in Firefox 67 and earlier, the origin of the page was defined as the directory from which the page was opened. Resources in the same directory and its subdirectories were treated as having the same origin for purposes of the CORS same-origin rule. X-Forwarded-For (XFF) ヘッダーは、 HTTP プロキシ又はロードバランサーを通過してウェブサーバーへ接続したクライアントの、送信元 IP アドレスを特定するために事実上の標準となっているヘッダーです。.
- To Force SSL Logins and SSL Admin Access
- Using a Reverse Proxy
- Further Information
- Virtual Hosts
To easily enable (and enforce) WordPress administration over SSL, there are two constants that you can define in your site’s wp-config.php file. It is not sufficient to define these constants in a plugin file; they must be defined in your wp-config.php file. You must also already have SSL configured on the server and a (virtual) host configured for the secure server before your site will work properly with these constants set to true.
Note: FORCE_SSL_LOGIN was deprecated in Version 4.0. Please use FORCE_SSL_ADMIN.
To Force SSL Logins and SSL Admin Access To Force SSL Logins and SSL Admin Access
The constant FORCE_SSL_ADMIN can be set to true in the wp-config.php file to force all logins and all admin sessions to happen over SSL.
Example Example
Using a Reverse Proxy Using a Reverse Proxy
If WordPress is hosted behind a reverse proxy that provides SSL, but is hosted itself without SSL, these options will initially send any requests into an infinite redirect loop. To avoid this, you may configure WordPress to recognize the HTTP_X_FORWARDED_PROTO header (assuming you have properly configured the reverse proxy to set that header).
Example Example
Further Information Further Information
The rest of this article serves as information in case you’re using an older version of WordPress (which ideally you shouldn’t!) or your SSL setup is somewhat different (ie. your SSL certificate is for a different domain).
Sometimes, you want your whole wp-admin to run over a secure connection using the https protocol. Conceptually, the procedure works like this:
- Set up two virtual hosts with the same url (the blog url), one secure, the other not.
- On the secure virtual host, set up a rewrite rule that shuttles all non-wp-admin traffic to the insecure site.
- On the insecure virtual host, set up a rewrite rule that shuttles all traffic to wp-admin to the secure host.
- Put in a filter (via a plugin) that filters the links in wp-admin so that once activated, administrative links are rewritten to use https and that edits cookies to work only over encrypted connections.
The following guide is for WordPress 1.5 and Apache running mod_rewrite, using rewrite rules in httpd.conf (as opposed to .htaccess files) but could easily be modified to fit other hosting scenarios.
Virtual Hosts Virtual Hosts
You need a (virtual) host configured for the secure server in addition to the non-secure site. In this example, the secure virtual host uses the same DocumentRoot as the insecure host. Hypothetically, you could use a host with a different name, such as wpadmin.mysite.com and link the document root to the wpadmin directory.
Please ask your ISP to set up a secure virtual host for you, or if you have administrative access set up your own. Note that you cannot use name based virtual hosting to identify different SSL servers.
Rewrite Rules For The Insecure Host Rewrite Rules For The Insecure Host
In the .htaccess or virtual host stanza in httpd.conf for your insecure host, add this rewrite rule to automatically go to the secure host when you browse to http://mysite.com/wp-admin/ or http://mysite.com/wp-login.php
This should go above the main wordpress rewrite block.
If you are using permalink rewrite rules, this line must come before RewriteRule ^.*$ - [S=40].

An important idea in this block is using THE_REQUEST, which ensures only actual http requests are rewritten and not local direct file requests, like an include or fopen.
Rewrite Rules For Secure Host (Optional) Rewrite Rules For Secure Host (Optional)
These rewrite rules are optional. They disable access to the public site over a secure connection. If you wish to remain logged in to the public portion of your site using the plugin below, you must not add these rules, as the plugin disables the cookie over unencrypted connections.
The secure virtual host should have two rewrite rules in an .htaccess file or in the virtual host declaration (see Using Permalinks for more on rewriting):
X Forwarded Firefox Settings
The first rule excludes the wp-admin directory from the next rule, which shuffles traffic to the secure site over to the insecure site, to keep things nice and seamless for your audience.
Setting WordPress URI Setting WordPress URI
For some plugins to work, and for other reasons, you may wish to set your WordPress URI in options to reflect the https protocol by making this setting https://mysite.com. Your blog address should not change.
Example Config Stanzas Example Config Stanzas
NOTE: The below config is not 100% compatible with WordPress 2.8+, WordPress 2.8 uses some files from the wp-includes folder. The redirection that the first set of Rewrite rules introduces may cause security warnings for some users. See https://core.trac.wordpress.org/ticket/10079 for more information.
Rewrite for Login and Registration Rewrite for Login and Registration
It is probably a good idea to utilize SSL for user logins and registrations. Consider the following substitute RewriteRules.
Insecure
Secure
Rewrite for sites running on port 443 or port 80 Rewrite for sites running on port 443 or port 80
Summary Summary
This method does not fix some inherent security risks in WordPress, nor does it protect you against man-in-the-middle attacks or other risks that can cripple secure connections.
However, this should make it much harder for a malicious person to steal your cookies and/or authentication headers and use them to impersonate you and gain access to wp-admin. It also obfuscates the ability to sniff your content, which could be important for legal blogs which may have drafts of documents that need strict protection.
Verification Verification
X Forwarded Firefox Download
On the author’s server, logs indicate that both GET and POST requests are over SSL and that all traffic to wp-admin on the insecure host is being shuttled over to the secure host.
Sample POST log line:
More testing, preferably with a packet sniffer and some hardcore network analysis tools, would help to confirm.
Limitations Limitations
The author assumes (but hasn’t checked) that if the user has stored cookies/told their browser to remember passwords (not based on form fields but if using certain external auth mechanism) and hits http://www.mysite.com/wp-admin/, those packets are sent in the clear and the cookie/auth headers could be intercepted. Therefore, to ensure maximum security, the user should explicitly use the https host or always log in at the beginning of new sessions.
HTTP pipelining is a technique in which multiple HTTP requests are sent on a single TCP (transmission control protocol) connection without waiting for the corresponding responses.[1]
The technique was superseded by multiplexing via HTTP/2,[2] which is supported by most modern browsers.[3]
As of 2018, HTTP pipelining is not enabled by default in modern browsers, due to several issues including buggy proxy servers and HOL blocking.[2]
Motivation and limitations[edit]
The pipelining of requests results in a dramatic improvement[4] in the loading times of HTML pages, especially over high latency connections such as satellite Internet connections. The speedup is less apparent on broadband connections, as the limitation of HTTP 1.1 still applies: the server must send its responses in the same order that the requests were received—so the entire connection remains first-in-first-out[1] and HOL blocking can occur. The asynchronous operation of HTTP/2 and SPDY are solutions for this.[5] Browsers ultimately did not enable pipelining by default, and by 2017 most browsers supported HTTP/2 by default which used multiplexing instead.[2]
Non-idempotent requests, like those using POST, should not be pipelined.[6] Sequences of GET and HEAD requests can always be pipelined. A sequence of other idempotent requests like PUT and DELETE can be pipelined or not depending on whether requests in the sequence depend on the effect of others.[1]
HTTP pipelining requires both the client and the server to support it. HTTP/1.1 conforming servers are required to support pipelining. This does not mean that servers are required to pipeline responses, but that they are required not to fail if a client chooses to pipeline requests.[7]
Implementation status[edit]
Pipelining was introduced in HTTP/1.1 and was not present in HTTP/1.0.[8]
Implementation in web servers[edit]

Implementing pipelining in web servers is a relatively simple matter of making sure that network buffers are not discarded between requests. For that reason, most modern web servers handle pipelining without any problem.
Implementation in web browsers[edit]
Of all the major browsers, only Opera based on Presto layout engine had a fully working implementation that was enabled by default. In all other browsers HTTP pipelining is disabled or not implemented.[5]
- Internet Explorer 8 does not pipeline requests, due to concerns regarding buggy proxies and head-of-line blocking.[9]
- Internet Explorer 11 does not support pipelining.[10]
- Mozilla browsers (such as Mozilla Firefox, SeaMonkey and Camino) support pipelining; however, it is disabled by default.[11][12] Pipelining is disabled by default to avoid issues with misbehaving servers.[13] When pipelining is enabled, Mozilla browsers use some heuristics, especially to turn pipelining off for older IIS servers.[14] Support for H1 Pipeline was removed from Mozilla Firefox in Version 54.[15]
- Konqueror 2.0 supports pipelining, but disabled by default.[citation needed]
- Google Chrome previously supported pipelining, but it has been disabled due to bugs and problems with poorly behaving servers.[16]
- Pale Moon (web browser) supports pipelining, and is enabled by default[17]
Implementation in web proxies[edit]
Most HTTP proxies do not pipeline outgoing requests.[18]
Some versions of the Squid web proxy will pipeline up to two outgoing requests. This functionality has been disabled by default and needs to be manually enabled for 'bandwidth management and access logging reasons.'[19] Squid supports multiple requests from clients.
X Forwarded Firefox To Yahoo
The Polipo proxy pipelines outgoing requests.[20]
Tempesta FW, an open source application delivery controller,[21] also pipelines requests to backend servers.[22]
Other implementations[edit]

The libwwwlibrary made by the World Wide Web Consortium (W3C), supports pipelining since version 5.1 released at 18 February 1997.[23]
Other application development libraries that support HTTP pipelining include:
X Forwarded Firefox Browser
- Perl modules providing client support for HTTP pipelining are HTTP::Async and the LWPng (libwww-perl New Generation) library.[24]
- Apache Foundation project HttpComponents provides pipelining support in the HttpCore NIO extensions.
- The Microsoft .NET Framework 3.5 supports HTTP pipelining in the module
System.Net.HttpWebRequest.[25] - Qt class
QNetworkRequest, introduced in 4.4.[26]
Some other applications currently exploiting pipelining are:
- IceBreak application server since BUILD389
- phttpget from FreeBSD (a minimalist pipelined HTTP client)[27]
- libcurl has limited support for pipelining using the CURLMOPT_PIPELINING option.[28]
- portsnap (a FreeBSDports tree distribution system)
- Advanced Packaging Tool (APT) support pipelining.[citation needed]
- Subversion (SVN) has optional support for HTTP pipelining with the serf WebDAV access module (the default module, neon does not have pipelining support).[29][30]
- Microsoft Message Queuing on Windows Server 2003 utilises pipelining on HTTP by default, and can be configured to use it on HTTPS.[31]
- IBM CICS 3.1 supports HTTP pipelining within its client.[32]
Multipart XHR is implementation of pipelining (without any browser or web server support) done purely in JavaScript in combination with server-side scripting.[citation needed]
Testing tools which support HTTP pipelining include:
- httperf[33]
X Forwarded Firefox To Google
See also[edit]
References[edit]
- ^ abc'Hypertext Transfer Protocol (HTTP/1.1): Message Syntax and Routing'. ietf.org. Retrieved 2014-07-24.CS1 maint: discouraged parameter (link)
- ^ abc'Revision 1330814 | Connection management in HTTP/1.x | MDN'. MDN Web Docs. Retrieved 2018-03-19.
- ^'HTTP2 browser support'. Retrieved March 9, 2017.CS1 maint: discouraged parameter (link)
- ^Nielsen, Henrik Frystyk; Gettys, Jim; Baird-Smith, Anselm; Prud'hommeaux, Eric; Lie, Håkon Wium; Lilley, Chris (24 June 1997). 'Network Performance Effects of HTTP/1.1, CSS1, and PNG'. World Wide Web Consortium. Retrieved 14 January 2010.CS1 maint: discouraged parameter (link)
- ^ abWillis, Nathan (18 November 2009). 'Reducing HTTP latency with SPDY'. LWN.net.
- ^'Connections'. w3.org.
- ^'HTTP/1.1 Pipelining FAQ''.
- ^'Archived copy'. Archived from the original on 2016-04-24. Retrieved 2016-04-16.CS1 maint: archived copy as title (link)
- ^'Wayback link of 'Windows Internet Explorer 8 Expert Zone Chat (August 14, 2008)''. Microsoft. August 14, 2008. Archived from the original on December 4, 2010. Retrieved May 10, 2012.CS1 maint: discouraged parameter (link)
- ^'Internet Explorer and Connection Limits'. IEBlog. Retrieved 2016-11-14.
- ^
- ^Cheah Chu Yeow. Firefox secrets. p. 180. ISBN0-9752402-4-2.
- ^'Bug 264354: Enable HTTP pipelining by default'. Mozilla. Retrieved September 16, 2011.CS1 maint: discouraged parameter (link)
- ^'Source code – nsHttpConnection.cpp'. Firefox source code. Mozilla. May 7, 2010. Retrieved December 5, 2010.CS1 maint: discouraged parameter (link)
- ^'Bug 1340655: Remove H1 Pipeline Support'. Mozilla. Retrieved March 22, 2017.CS1 maint: discouraged parameter (link)
- ^HTTP Pipelining - The Chromium Projects
- ^'HTTP/1 Pipelining support has been removed in Firefox 54 - Pale Moon forum'. forum.palemoon.org. Retrieved 2018-06-07.
- ^Mark Nottingham (June 20, 2007). 'The State of Proxy Caching'. Retrieved May 16, 2009.CS1 maint: discouraged parameter (link)
- ^'squid : pipeline_prefetch configuration directive'. Squid. November 9, 2009. Retrieved December 1, 2009.CS1 maint: discouraged parameter (link)
- ^'Polipo — a caching web proxy'. Juliusz Chroboczek. September 18, 2009. Retrieved November 12, 2009.CS1 maint: discouraged parameter (link)
- ^'Tempesta FW — a Linux Application Delivery Controller'. GitHub. Retrieved March 29, 2018.CS1 maint: discouraged parameter (link)
- ^'Servers: Tempesta's side - tempesta-tech/tempesta Wiki'. Tempesta Technologies INC. August 1, 2017. Retrieved March 29, 2018.CS1 maint: discouraged parameter (link)
- ^Kahan, José (June 7, 2002). 'Change History of libwww'. World Wide Web Consortium. Retrieved August 3, 2010.CS1 maint: discouraged parameter (link)
- ^'Using HTTP::Async for Parallel HTTP Requests (Colin Bradford)'(PDF). Archived from the original(PDF) on 2012-03-10. Retrieved 2010-08-03.
- ^System.Net.HttpWebRequest & pipelining
- ^QNetworkRequest Class ReferenceArchived 2009-12-22 at the Wayback Machine, Nokia QT documentation
- ^Pipelined HTTP GET utility
- ^Curl pipelining explanationArchived 2012-06-27 at the Wayback Machine, Curl developer documentation
- ^C. Michael Pilato; Ben Collins-Sussman; Brian W. Fitzpatrick (2008). Version Control with Subversion. O'Reilly Media. p. 238. ISBN0-596-51033-0.
- ^Justin R. Erenkrantz (2007). 'Subversion: Powerful New Toys'(PDF).
- ^'HTTP/HTTPS messages'. Microsoft TechNet. January 21, 2005.
- ^How CICS Web support handles pipelining
- ^'HTTP Website'. Archived from the original on 2012-06-08. Retrieved 2010-10-01.
External links[edit]
- RFC 7230 'Hypertext Transfer Protocol (HTTP/1.1): Message Syntax and Routing'. ietf.org. Retrieved 2014-07-24.CS1 maint: discouraged parameter (link)
- serf C library